QUESTION 145
You have a Microsoft Azure Active Directory (Azure AD) tenant.
Some users signs in to that computer by using Windows hello for Business.
A user User1 purchases a new computer and joins the computer to Azure AD.
User1 attempts to configure the sign-in options and receives the error message shown in the exhibit. (Click the Exhibit tab.)
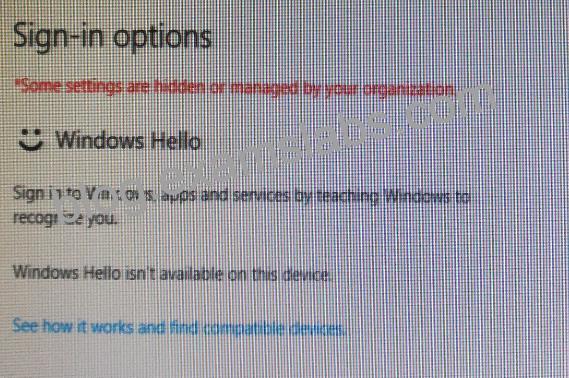
You open device Manager and confirmed that all the hardware works correctly.
You need to ensure that user1 can use Windows Hello for Business facial recognition to sign in to the computer.
What should you do first.
Topic 1, Contoso, Ltd
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has IT, human resources (HR), and finance departments.
Contoso recently opened a new branch office in San Diego. All the users in the San Diego office work from home.
Existing environment
Contoso uses Microsoft 365.
The on-premises network contains an Active Directory domain named contoso.com. The domain is synced to Microsoft Azure Active Directory (Azure AD).
All computers run Windows 10 Enterprise.
You have four computers named Computer1, Computer2, Computer3, and ComputerA. ComputerA is in a workgroup on an isolated network segment and runs the Long Term Servicing Channel version of Windows
10. ComputerA connects to a manufacturing system and is business critical. All the other computers are joined to the domain and run the Semi-Annual Channel version of Windows 10.
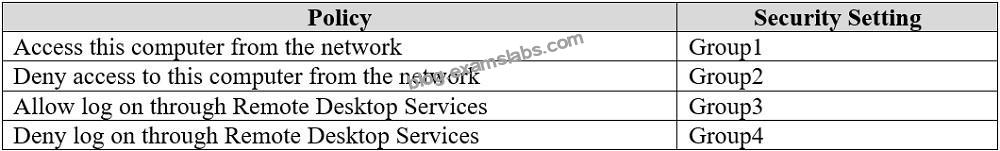
In the domain, you create four groups named Group1, Group2, Group3, and Group4.
Computer2 has the local Group Policy settings shown in the following table.
The computers are updated by using Windows Update for Business.
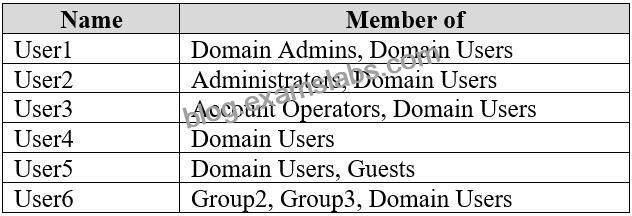
The domain has the users shown in the following table.
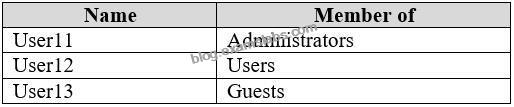
Computer1 has the local users shown in the following table.
Requirements
Planned Changes
Contoso plans to purchase computers preinstalled with Windows 10 Pro for all the San Diego office users.
Technical requirements
Contoso identifies the following technical requirements:
* The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
* Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers.
* Users in the HR department must be able to view the list of files in a folder named D:\Reports on Computer3.
* ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.
* Quality update installations must be deferred as long as possible on ComputerA.
* Users in the IT department must use dynamic look on their primary device.
* User6 must be able to connect to Computer2 by using Remote Desktop.
* The principle of least privilege must be used whenever possible.
* Administrative effort must be minimized whenever possible.
* Assigned access must be configured on Computer1.







Leave a Reply